Many articles have already been written about how a much larger number of sites are subject to non-targeted hacker attacks than targeted attacks. According to statistics, only about 25% of website hacks are targeted in nature, while the rest “get caught” on the hook randomly.
The most common mistake that makes it easier for hackers to hack a site is the vulnerability of CMS, plugins, or templates. Any, even the slightest, “crack” in the system significantly reduces the security level of the site. If you get caught, be prepared for the fact that your page will be used for unintended purposes, it can turn into a center for distributing advertising and spam.
If you think this will pass you by, you are deeply mistaken. Finding sites with problem areas in CMS is quite simple. Even a non-professional, but novice hacker can do this. Google Hacking Database is a so-called registry of sites vulnerable by identical signs. How does it work? Indexed sites with certain vulnerabilities are found by hackers in search engines, thanks to which they get access to upload malicious code.
Based on this, it’s worth understanding that if there is even the slightest flaw in the CMS or installed plugins, hacking the site will not be difficult. The owner or webmaster must take care of a sufficient level of site protection.
How to Hack a Site Using Google’s Capabilities
To demonstrate to trusting or self-confident owners that hacking a site in a few minutes is possible simply by using Google’s functions, we decided to give a visual example of how successfully hackers use the mistakes you can make when creating a site.
Since September 2015, the Google Hacking Database has added the ability to search for pages with open directories where you can view all files, including access credentials and passwords. To do this, you simply need to:
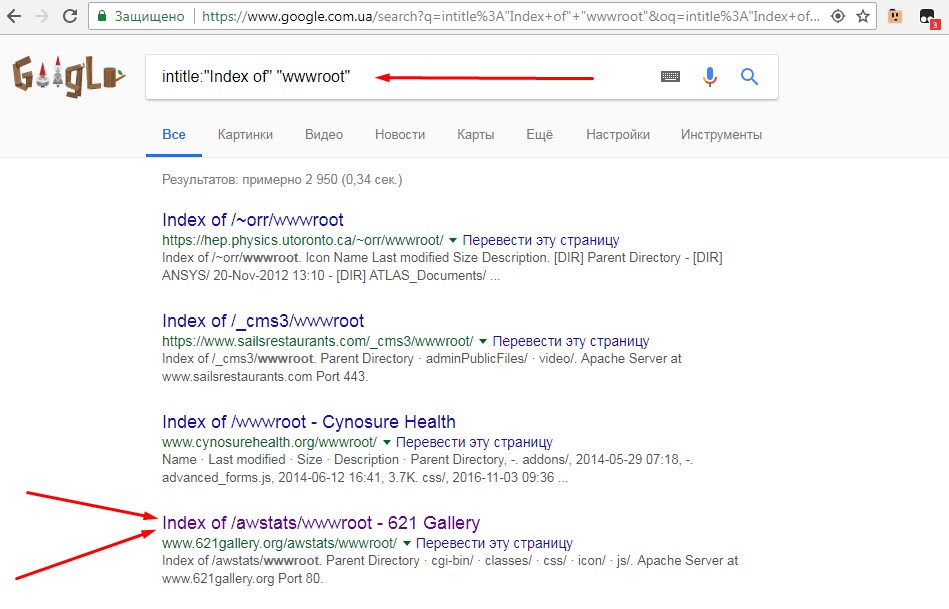
Send the query intitle:”Index of” “wwwroot to the Google search engine, and we get a complete list of sites with open directories. Next, you need to select the site we need and follow the link.
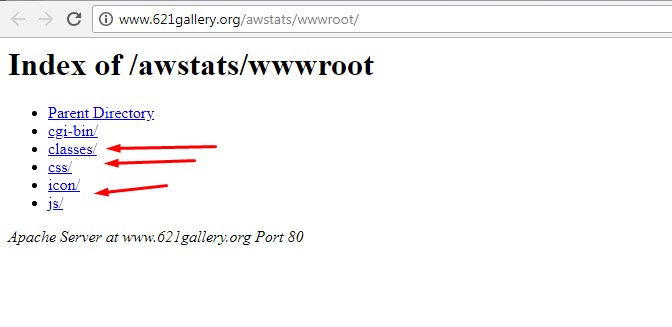
This link will open the entire list of directories. You can browse through them and find the serverconfig.xml file – it contains all logins and passwords for databases. If the credentials also match SSH and FTP, then the hacker will have access to the server itself.
The entire procedure takes no more than a few minutes (this is for a beginner). A hacker who knows their business can perform these actions automatically in just a few seconds.
How to Prevent Website Hacking
Of course, no one wants to find themselves in such an unpleasant situation. It’s especially offensive when the system is hacked due to minor flaws that could have been eliminated initially, but over time brought many troubles. Therefore, immediately after creating a site, it’s better to seek help from professionals. Ukrhost company provides not only hosting placement and domain registration services, but also site maintenance during operation. A team of professionals will initially install modern protection from hacking and will monitor the security of your page 24 hours a day!