The root of the evils that cause viruses, annoying advertising, and infected files to appear is the desire to get rich at someone else’s expense. If you have learned that a virus is already roaming around your hosting or VPS, most likely web server protection is not installed, which means dealing with intruders is much more difficult.
What to Do If Your Site is Infected?
Malicious signatures that should be searched for can be encrypted code inserted into the page code. Thus, in the absence of antivirus on the server or its outdated version, identifying such an element will be problematic.
So, you have an infected virtual server.
- The server antivirus needs to be updated to the latest version, or possibly reinstalled entirely. This will be the first step.
- Step two – changing server access. By changing all passwords and SSH keys (if any), you reduce the likelihood of the virus infection situation recurring. After completing the procedure, entrust new access only to trusted specialists and protect it as you would the key to your home.
- You can only protect yourself and ensure complete server protection by taking all necessary measures. This means that the next, third, stage of web server protection is checking the site, identifying all infected software files, and removing viruses.
- The fourth step on the path to protecting the server from hacking will be updating plugins, templates, modules, and CMS on your sites.
- At the final fifth stage, ukrhost always recommends checking the list of running processes by connecting via SSH and executing the pstree command.
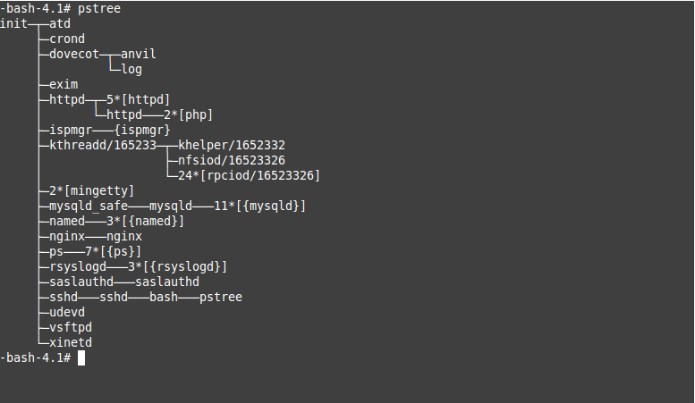
In this example, you can see that the “ps” process is running under the name “ps”, and the original one runs under bash. We conclude that this is a virus. Pay special attention to outgoing connections, which can be checked with the lsof -i command, as well as the directories where processes are running.
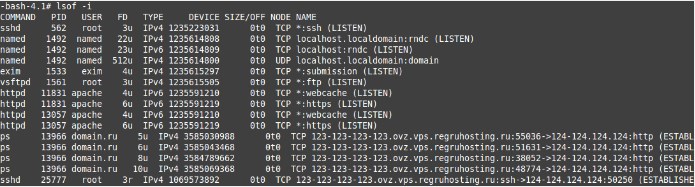
As can be seen from this screenshot, the process we discovered is generating strange outgoing connections. You need to determine the directory from which it is launched and delete it.
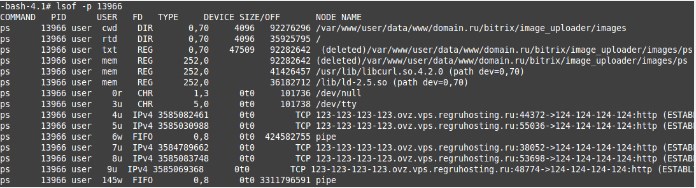
We run:lsof -p ID // где Id - это pid процесса
Pay attention to the lines with cwd and txt values in the FD column, that’s where the launch directory of this infection will be indicated.
Don’t forget to conduct data analysis or systematically increase the security level on your virtual server.